With the surge in cyberattacks, the Singapore government with the Cyber Security Agency of Singapore (CSA) have been issuing public advisories on steps for organisations to safeguard their business. One recommendation worth noting is the adoption of a ‘Zero Trust’ cybersecurity posture. This is in response to recent trends including remote working, BYOD, and cloud-based assets that are not located within an organisation’s network boundary.
So what is Zero Trust?
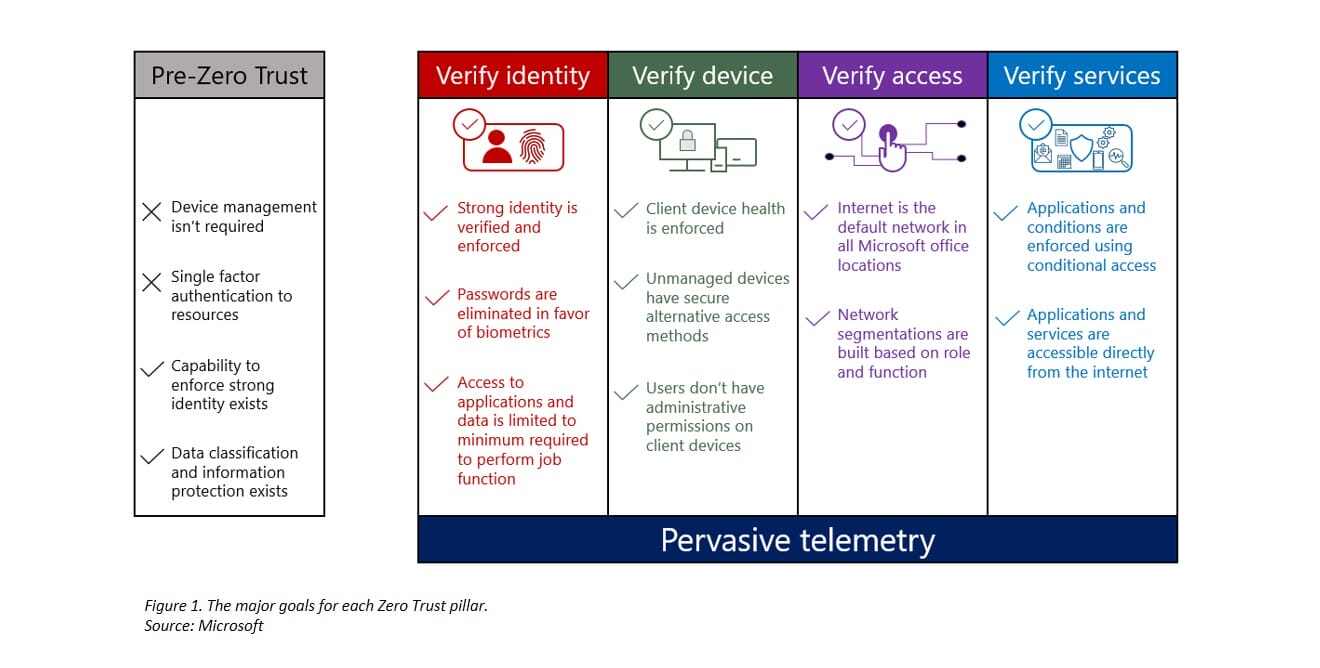
Zero Trust is a security framework centred on the belief that organisations must verify everything that is trying to connect to its system before granting access, including those already inside its network. Simply put, do not trust anything by default.
Zero Trust confronts older security practices where individuals or devices with prior network access are automatically trusted while those outside of the network are not. Hackers therefore are able to exploit this loophole to navigate through internal systems with little resistance once they breached corporate firewalls.
Why is Zero Trust needed?
As organisations move to the cloud and attackers get smarter and more sophisticated, it is becoming increasingly challenging to secure one’s assets. Unsecured gateways, exploitable cloud VPNs, and outdated firewalls, are just some of the many cloud risks, which Zero Trust can mitigated.
While Zero Trust security does not protect networks from every possible attack, it can significantly reduce risks, speed up threat detection and close the visibility gaps.
5 tips when implementing Zero Trust
1 | Reduce attack surface
Identify users with access to critical systems and data that are most likely to be targeted by attackers. You do not have infinite resources and money to secure everything, so knowing who is accessing the most valuable data, and how they are being accessed, will help you to balance risks.
2 | Verify explicitly and validate continuously
Multifactor Authentication (MFA) is the first control you should implement. End users must be authenticated, authorised, and validated in real time and on an ongoing basis to ensure that they always have the proper privileges. To encourage MFA adoption, have flexible authentication options such as passwordless authentication and biometrics so user can select what works best for them.
3 | Allow just enough access
For all valuable resources, minimise the number of accounts, local administrative access, users with access to accounts (both human and machine), and their privileges. You should also establish processes to regularly remove unnecessary privileges and accounts, and restrict software installations with endpoint protection technology.
4 | Consider user experience
Authentication processes helps to maintain high levels of security but it may cause obstacles in workflows and hamper employee productivity. The key here is to balance convenience and security. Identify every aspect of the flow process, and understand how it impacts the user, so you can create a secure environment conducive to a frictionless experience.
5 | Drive a cultural change
Zero trust is more than just a set of controls. It is a mindset that requires a cultural shift. To maintain cyber resilience, you need to actively engage and have the support of everyone, especially the non-IT staff in your organisation. Take time to educate staff on the importance of security and the need for everyone to play their part in the cyber protection.
Need help?
It is important to note that Zero Trust is not a one-size-fits-all solution, but a proactive security approach. To maintain a competitive advantage in today’s cloud era, business leaders can look to Zero Trust for a long-term defence framework that provides robust security by continuously evaluating risks and controlling access.
Need help to transform your security and networking while ensuring data protection for your mobile workforce? Speak to us now.